Ports is a tool that detects if there are any opened ports ( TCP or UDP ). When the dialog appears All Ports radio button is selected. This means that all available ports will be shown. Each field in the row contains port specific information.
Service contains service name that uses the specified port.
Port is the port number.
Proto describes the protocol used for the connection.
Trojan contains the name of trojan assoccieted with port.
Desciption is description of service using specified port.
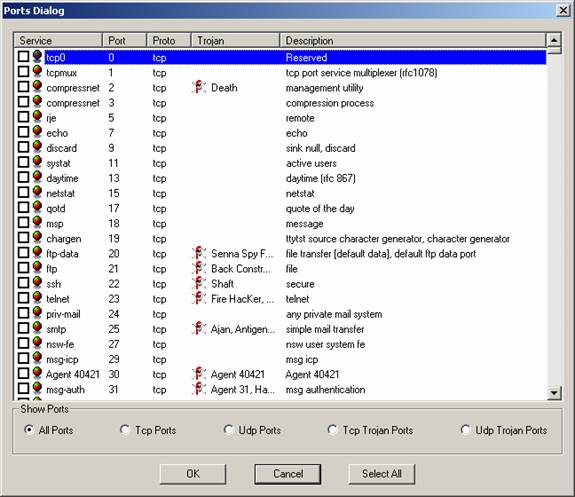
To filter the ports change the selected radio button.
Tcp Ports will show only the services using Tcp connection.
Udp Ports will show only the services using Udp connection.
Tcp Trojan Ports will show only services using Tcp Trojans.
Udp Trojan Ports will show only services using Udp Trojans.
To select all ports click on the Select All button.
To deselect all ports click on the same radio button. |

